How to Effortlessly Make a USB bootable KALI Linux with persistence using YUMI from within Windows. KALI Linux, based on Debian, is designed specifically for penetration testing. It includes a vast selection of security tools such as network analyzers, password crackers, wireless tools, and fuzzers, making it ideal for cybersecurity.
KALI Linux Live Bootable USB with Persistence
Distribution Website: Project Page
Persistent Feature: Yes
About KALI Linux
KALI Linux is a powerful penetration testing tool built on Debian, serving as the successor to Backtrack Linux, which was discontinued in March 2013. While Backtrack was based on KNOPPIX, KALI carries forward its legacy with a similar array of cybersecurity tools, tailored specifically for security professionals and ethical hackers.
Since its release, KALI Linux has become a go-to platform for penetration testing, offering over 600 pre-installed security tools, such as Metasploit, Nmap, Wireshark, and John the Ripper. These tools cover a wide range of testing scenarios, from network analysis to password cracking, making KALI an invaluable resource for cybersecurity professionals. Users can also choose from multiple desktop environments, including KDE, XFCE, and GNOME, for a customizable experience based on personal preferences or system requirements.
One of KALI’s standout features is its persistence capability, allowing users to save files, configurations, and other data across reboots, making it especially useful for USB installations. Additionally, KALI follows a rolling release model, which ensures continuous updates to its tools and the OS, keeping it relevant in the rapidly evolving field of cybersecurity.
As a free and open-source platform, KALI encourages customization and community-driven development, empowering users to modify and adapt the distribution to meet their needs. Whether you’re an experienced security professional or just beginning your journey in ethical hacking, KALI Linux offers a robust, regularly updated, and highly portable penetration testing solution.
What is USB Persistence?
Having a KALI Linux Live USB with persistence allows you to retain files, data configurations, and setups across reboots. This is implemented using the Debian persistence method. It involves creating a persistent partition or block file formatted as ext3 or ext4 with the label persistence, containing a persistence.conf file with the line: / union.
YUMI simplifies this process by automatically creating the necessary persistence file for you during the preparation of your USB stick.
YUMI Essentials to make a KALI Linux Live USB
-
- YUMI exFAT (for Live Linux USB creation)
- KALI Linux ISO file
- High Speed USB Flash Drive 8 GB +
- Windows 11, 10, or 8
- Computer that supports booting from USB via UEFI or BIOS
How to Make a KALI Linux Bootable USB via YUMI
This tutorial explains how to create a KALI Linux Bootable USB for penetration testing. Here, we’re using the YUMI exFAT tool, but you can also use the Universal USB Installer if you prefer, as both tools are very similar and function exactly the same.
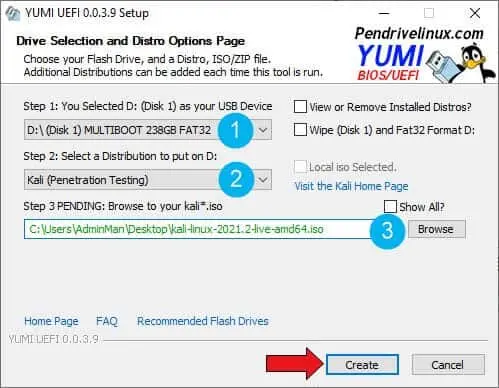
- Download and launch YUMI exFAT Bootable USB Creator.
- Configure YUMI:
- Select your USB drive from the device list, then check prepare the device.
- Choose "Kali (Penetration Testing)" from the distribution list.
- Browse to your KALI Linux ISO file.
- Click "Create" to start the process.
- Set BIOS/UEFI to Boot from USB: Restart your computer, enter BIOS or the boot menu, and select your USB drive as the first boot device.
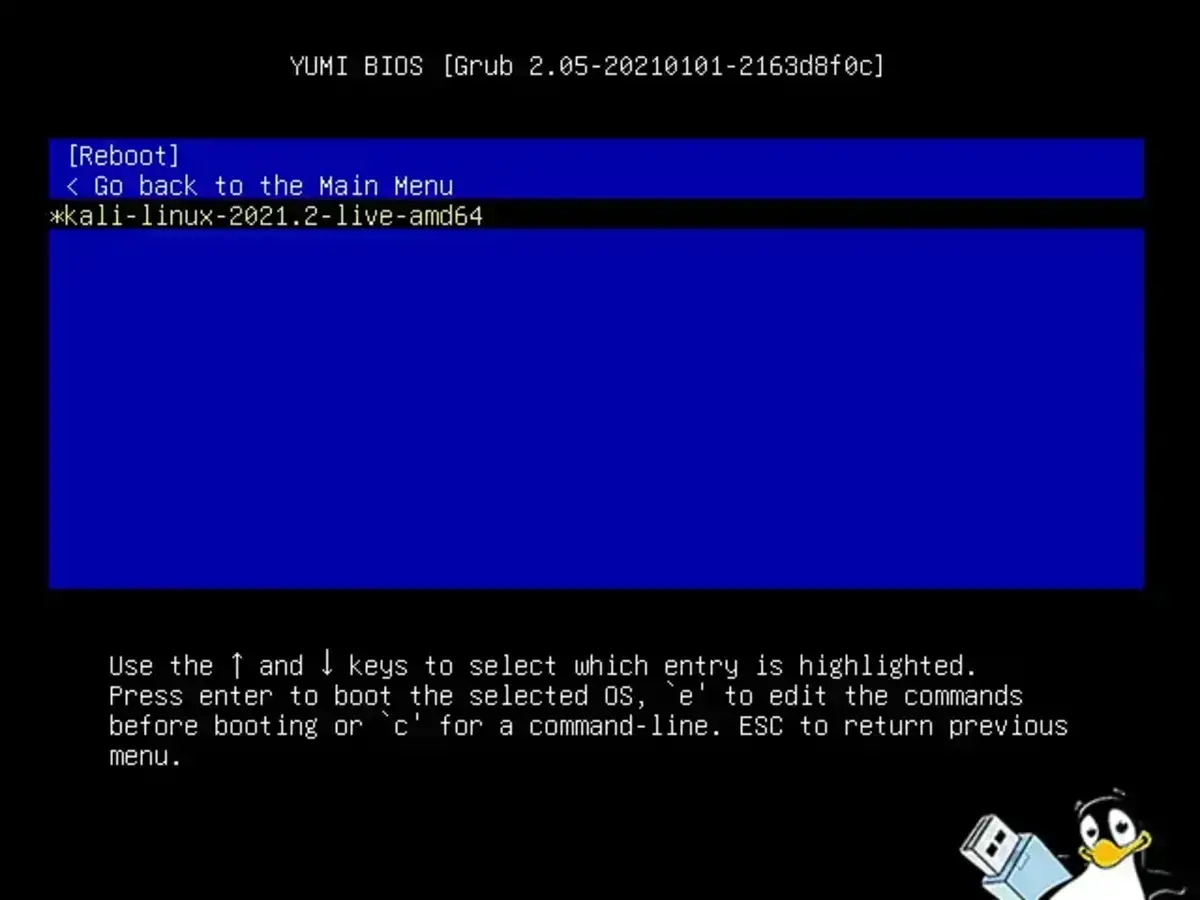
- Boot into your KALI Linux bootable USB: If all went well, you should see the YUMI Boot Menu with an option to select and run KALI Linux from your USB drive.
Default Username and Password for KALI Linux
- Username: kali
- Password: kali
How to Make a KALI Linux Bootable USB on Linux
In addition to using YUMI on Windows, Linux users can create a bootable KALI USB with persistence using the dd command. This method directly writes the KALI Linux ISO file to the USB drive, creating a bootable image. Persistence can then be added manually by creating a persistent partition on the USB.
Linux Requirements to make a KALI Linux USB
- KALI Linux ISO file
- A Fast USB stick (8GB or larger recommended)
- A Linux system with
ddcommand - Access to
gpartedor a similar partitioning tool (optional) - Computer that supports booting from USB via UEFI or BIOS
Steps to Create a Bootable KALI Linux USB with dd
- Insert your USB drive and identify its device name. Run the following command to list all connected drives:
sudo fdisk -l
Note the device name (e.g.,
/dev/sdX), whereXrepresents the drive letter. Make sure you have the correct device name as theddcommand will overwrite data on the specified device. - Write the KALI Linux ISO to the USB drive using
dd:sudo dd if=/path/to/kali-linux.iso of=/dev/sdX bs=4M status=progress
Replace
/path/to/kali-linux.isowith the path to your KALI Linux ISO file, and/dev/sdXwith your USB drive's device name. The process can take a few minutes. - Once
ddcompletes, you will have a bootable KALI Linux USB. To add persistence, follow these additional steps.
Adding Persistence to Your KALI Linux Live USB
- Open
gparted(or a similar partitioning tool) and select your USB drive. - Create a new partition in the unallocated space on the USB. Format this partition as ext4 and label it persistence.
- Once formatted, mount the new persistence partition. Then, create a file called
persistence.conf:echo "/ union" | sudo tee /mnt/persistence/persistence.conf
This configuration enables the persistence feature by specifying that changes should be saved across reboots.
- Unmount the partition, and your KALI Linux USB is now configured with persistence. Boot from this USB and select the "Live USB Persistence" option to enable saving of data across sessions.
This dd method is an effective way to create a bootable KALI Linux USB directly from Linux. It's especially useful for those comfortable with command line operations and offers more control over partitioning for persistence.
KALI Frequently Asked Questions (FAQ)
Here are some answers to the most commonly asked questions we get regarding this distribution and YUMI.
Can I install additional software on KALI Linux with persistence?
Yes, with persistence, you can install some software, save most configurations, and store files that will be retained even after rebooting.
Why use YUMI instead of other USB tools?
You could use other tools to make a Kali Linux bootable USB. However, YUMI is optimized for creating persistent USB drives and supports multiboot functionality, allowing multiple OS installations on one USB. It also allows you to continue to use your USB stick for traditional storage purposes.
Does KALI Linux work on all USB flash drives?
This Live Linux distribution works best with fast USB drives. Using a USB 3.0 or higher flash drive can greatly improve performance, and larger USB sticks are especially useful for storing larger persistence files.
Can I boot KALI Linux on both UEFI and Legacy systems?
Yes, YUMI supports both UEFI and BIOS boot modes, making it compatible with both modern and most older computers.
Though there might be other methods, creating a KALI Linux bootable USB with persistence is straightforward with YUMI exFAT. This setup provides a portable penetration testing environment, ideal for professionals or beginners in ethical hacking. Aside from making a Kali Linux bootable USB with persistence, YUMI can also be used to create multiboot flash drives, allowing you to store and run multiple operating systems, antivirus tools, and utilities on one single device.
Alternative to KALI Linux: Parrot Security OS
While KALI Linux is a popular choice for penetration testing and ethical hacking, another alternative is Parrot Security OS. Parrot is a Linux based distribution that not only focuses on penetration testing but also offers additional tools for privacy protection, digital forensics, and cryptography. Below, we compare the two to help you choose the best one for your needs.
Main differences between the two are charted below:
| Feature | KALI Linux | Parrot Security OS |
|---|---|---|
| Base Distribution | Debian | Debian |
| Primary Focus | Penetration testing, security auditing, vulnerability assessment | Penetration testing, privacy protection, digital forensics, cryptography |
| Toolset | Over 600 pre-installed tools focused on penetration testing (e.g., Metasploit, Nmap, Wireshark, John the Ripper) | Wide range of tools for penetration testing, privacy (e.g., Tor, Anonsurf, I2P), and digital forensics |
| Privacy & Anonymity Features | None (focused on testing and exploiting vulnerabilities) | Includes tools for anonymity such as Tor, I2P, and Anonsurf for enhanced privacy protection |
| Performance & System Requirements | Lightweight, optimized for lower-end hardware (XFCE desktop environment by default) | More resource-intensive due to additional privacy tools and features (MATE desktop environment by default) |
| Desktop Environment | XFCE (lightweight) or GNOME/KDE (optional) | MATE (lightweight), KDE (feature-rich), or LXQt (fast and efficient) |
| Additional Features | Focused primarily on penetration testing and security auditing | Supports privacy tools, digital forensics, and cryptography alongside penetration testing tools |
| Community & Support | Large, active community with extensive resources | Smaller but growing community with a focus on privacy and forensics |
Both KALI Linux and Parrot Security OS offer strong security features, but they cater to slightly different use cases. If you’re looking for a focused, reliable toolset specifically for penetration testing and security auditing, KALI Linux is a great choice. However, if you need a security distribution with a stronger emphasis on privacy, anonymity, and digital forensics alongside traditional penetration testing, then Parrot Security OS might be a better fit for you.
Final Notes on Creating a USB KALI Linux
By following this tutorial, you should now have successfully created a USB KALI Linux with the optional persistence feature using YUMI on Windows or the dd command from Linux. This setup allows you to carry a fully functional penetration testing environment wherever you go, with the added benefit of saving files, configurations, and installed tools across reboots.
Why This Method Stands Out
- Easy & Efficient – YUMI automates the process, while
ddprovides full control for Linux users. - Persistent Storage – Retain your work and configurations.
- UEFI & Legacy Boot Support – Ensuring compatibility with modern and older systems.
- Multiboot Capability – YUMI allows you to add multiple OS installations on one USB drive, so you're not limited to just KALI.
Whether you're a cybersecurity professional, ethical hacker, or enthusiast, this method provides a portable, flexible, and reliable way to run KALI Linux from USB. If you encounter issues, ensure you're using a high speed USB drive and the latest KALI Linux ISO for optimal performance. Now that your bootable USB is ready, it's time to explore, test, and enhance your cybersecurity skills!
