Add User to Sudoers File in Linux: Adding a user to the sudoers file or wheel group is an essential step for granting administrative (root) privileges on a Linux system. In this guide, you will learn how to safely add a user to the sudoers file using group membership or the visudo command, which is the recommended and safest way to manage sudo permissions.
Whether you are using Ubuntu, Debian, Fedora, Arch, CentOS, openSUSE, or Gentoo, the steps below include distro specific instructions that work across modern Linux systems.
Add User to Sudoers: Grant Administrative (Root) Access
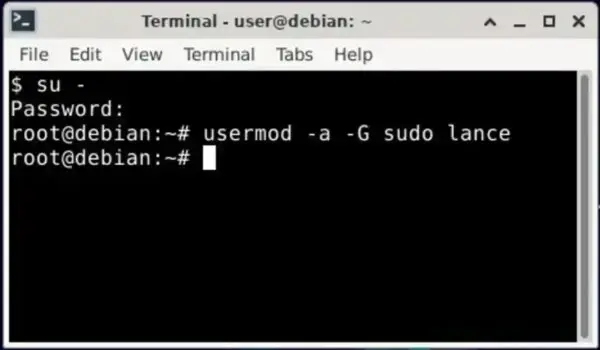
Using the terminal to add a user to the sudoers file on Debian based systems like Ubuntu.
Quick Summary: Add a User to Sudoers
- Ubuntu and Debian:
usermod -aG sudo username - Fedora, CentOS, Arch, openSUSE:
usermod -aG wheel username - Edit sudoers safely using
sudo visudo - Manual entry:
username ALL=(ALL) ALL - Verify access with
sudo whoamiorsudo -l
On Debian and Ubuntu based systems, users in the sudo group are allowed to execute commands as root. Other Linux distributions typically rely on the wheel group for the same purpose.
Important:
Some Live Linux environments do not have a root password set by default. If you are using a Live system, you may need to set a root password before continuing. See how to set the default root password for Debian or Ubuntu.
Set a Root Password (If Required)
If the root account is disabled, set a password first.
- Open a terminal with Ctrl + Alt + T
- Run the following command:
sudo passwd rootOnce completed, continue with the instructions below.
Add a User to Sudoers on Ubuntu and Debian
- Open a terminal: Ctrl + Alt + T
- Switch to the root account:
sudo su- Add the user to the sudo group (replace
username):
usermod -aG sudo usernameNote: The user must log out and log back in before group changes take effect.
Fix "bash: sudo: command not found"
If you encounter the error bash: sudo: command not found, install sudo as root.
apt -y install sudoThen test sudo access.
su - username sudo whoamiEditing the Sudoers File with visudo
Direct edits to /etc/sudoers are risky. Always use visudo to prevent syntax errors.
- Open a terminal
- Run:
sudo visudo- Scroll to the bottom of the file
- Add the following line:
username ALL=(ALL) ALL- Save and exit: Ctrl + X, Y, Enter
Tip: To make editing easier:
export EDITOR=nanoGranting Sudo Access on Other Linux Distributions
The following instructions show how to add a user to the sudoers file on other popular Linux distributions.
CentOS: Add User to Sudoers (wheel group)
- Switch to root:
su -- Add the user to the wheel group:
usermod -aG wheel username- Verify sudo access:
su - username sudo whoamiArch Linux: Add User to Sudoers
- Install sudo:
pacman -S sudo- Edit the sudoers file:
EDITOR=nano visudo- Uncomment the following line:
%wheel ALL=(ALL) ALL- Add the user to the wheel group:
usermod -aG wheel usernameFedora: Add User to Sudoers
Fedora includes sudo by default. You only need to add the user to the wheel group.
usermod -aG wheel usernameConfirm the wheel group is enabled:
sudo visudoEnsure this line is uncommented:
%wheel ALL=(ALL) ALLopenSUSE: Add User to Sudoers
zypper install sudo usermod -aG wheel usernameGentoo: Add User to Sudoers
emerge --ask app-admin/sudo usermod -aG wheel usernameFrequently Asked Questions
What is the sudoers file?
The sudoers file defines which users or groups can run commands with elevated privileges using sudo.
What is the wheel group?
The wheel group is a special administrative group used by many Linux distributions to grant sudo access.
Why should I use visudo?
visudo validates syntax before saving and prevents configuration errors that could lock you out of admin access.
How do I verify sudo access?
Run sudo whoami or sudo -l. If you see root privileges listed, sudo is working correctly.
Can I remove sudo access later?
Yes. Remove the user from the sudo or wheel group or delete the entry using visudo.
Best Practices When Managing Sudo Access
- Always edit sudoers using
visudo - Prefer group based access over individual user entries
- Grant sudo access only to trusted users
- Avoid using
NOPASSWDunless absolutely necessary
Final Thoughts
Granting sudo access gives users full administrative control over a Linux system. When done correctly using groups and the sudoers file, it provides both flexibility and security. Follow these steps carefully and you can safely manage user privileges across nearly any Linux distribution.
